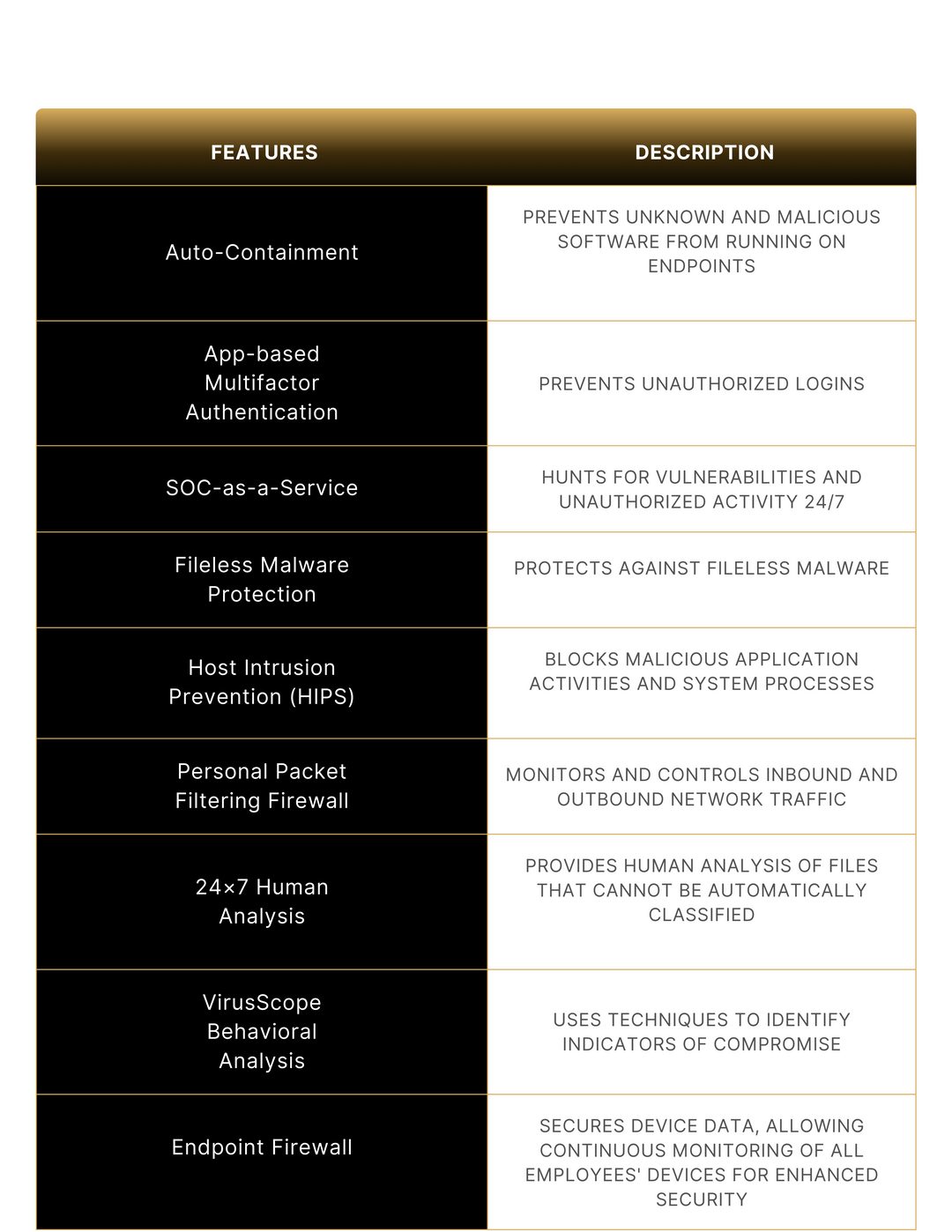
Why AMEOT Sentry in a class all its own.
The anatomy of a ransomware attack on a large organization with a complex network typically involves the following steps:
Initial access: The attackers gain initial access to the organization's network through a variety of methods, such as phishing, exploiting vulnerabilities, Brute Force or using stolen credentials.
Lateral movement: Once the attackers have gained initial access, they will move laterally through the network to identify and compromise high-value systems. This may involve using compromised credentials, exploiting vulnerabilities, or abusing legitimate access privileges.
Escalation of privilege: The attackers will escalate their privileges to gain administrative access to critical systems. This will allow them to encrypt files and disrupt operations.
Data exfiltration: The attackers will exfiltrate encrypted data from the organization's network. This may be done through a variety of methods, such as transferring the data over the internet or using removable media.
Ransom demand: The attackers will then demand a ransom payment from the organization in exchange for the decryption key.
AMEOT Sentry uses a comprehensive approach to stopping ransomware attacks. It addresses all of the key steps in the attack process and includes a number of features that can help to prevent attacks from succeeding